Traffic matrices have been around for a long time as detailed in this
article. A cell in the matrix denotes a quantity of traffic flowing from a
source to a destination. Partitioning each of the source and destination
dimensions into interesting subsets allows to draw conclusions about
traffic flowing into and out of those subsets. For example, traffic flowing
into and out of a company network, or along geographic or organizational
boundaries.
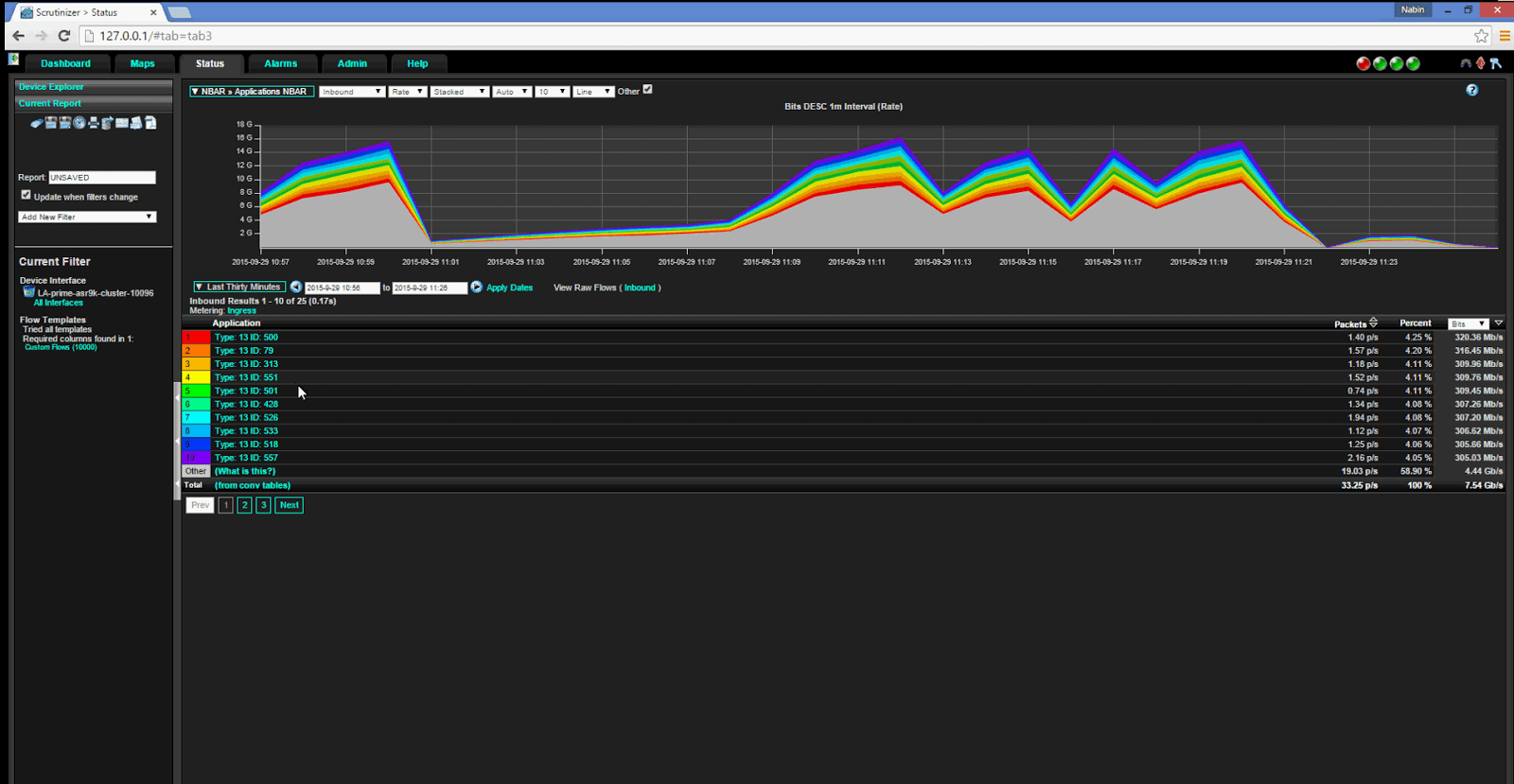
With the advent of NetFlow and Cisco's NBAR the 2-dimensional source
IP/destination IP (network traffic) matrices have been extended to add
the application dimension: not only do we know how much traffic flows
between network nodes, but also which kind. For example, we can
quantify how much Youtube traffic flows in and out of the company network
vs. plain web-surfing or shopping.
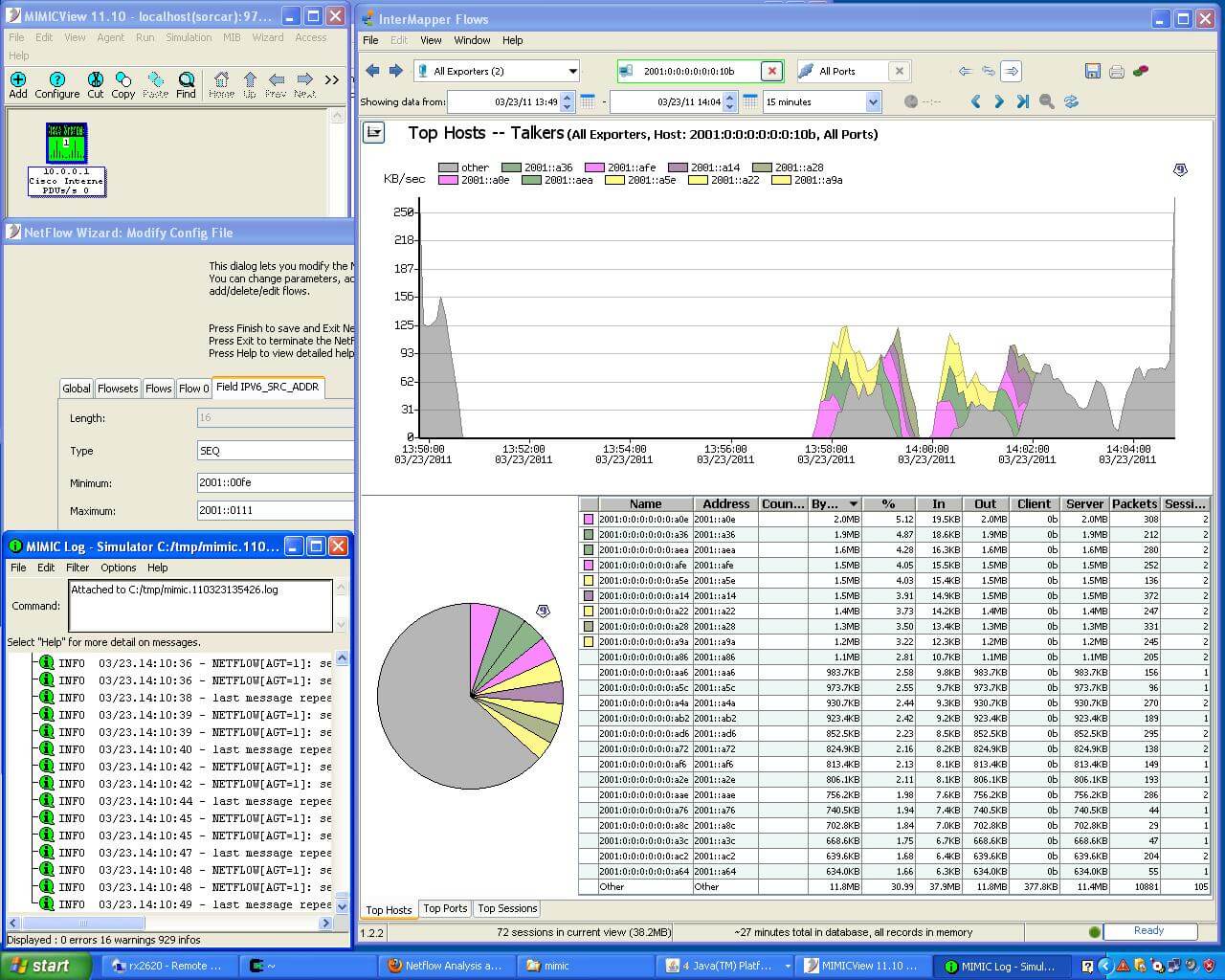
MIMIC NetFlow Simulator can simulate any flow matrix for network
performance and security monitoring. In a vast sea of normal traffic
flows slight deviations can be added deterministically to test and
demonstrate performance monitoring features or security policies.
For example, MIMIC is being used to shape application traffic for
StealthWatch, Scrutinizer, Intermapper, and even in the on-demand
demo cloud for Cisco's dCloud.
Friday, September 16, 2016
Wednesday, September 14, 2016
Test your management application with hundreds of Dell iDRACs
Testing your configuration management application or data center
orchestration software for large scalability requires you to setup a
large lab with many servers.
In the case of Dell servers, the Dell iDRAC is a card with out-of-band
control and monitoring of a Dell server. Rather than buying many servers
and hardware, you can simulate the iDRAC and server in MIMIC Web Simulator.
The screenshot below shows the Dell OpenManage Essentials application
managing 100 simulated Dell servers. The simulation allows complete
control to achieve whatever testing or demo scenario you want.
Once simulated in MIMIC, each of these devices are available on
the network as if they are real devices. Your management applications
can access them and have a complete control over their configurations.
You can easily start, stop them and change their parameters at
run time. You can customize the simulation at run-time to introduce
faults.
orchestration software for large scalability requires you to setup a
large lab with many servers.
In the case of Dell servers, the Dell iDRAC is a card with out-of-band
control and monitoring of a Dell server. Rather than buying many servers
and hardware, you can simulate the iDRAC and server in MIMIC Web Simulator.
The screenshot below shows the Dell OpenManage Essentials application
managing 100 simulated Dell servers. The simulation allows complete
control to achieve whatever testing or demo scenario you want.
Once simulated in MIMIC, each of these devices are available on
the network as if they are real devices. Your management applications
can access them and have a complete control over their configurations.
You can easily start, stop them and change their parameters at
run time. You can customize the simulation at run-time to introduce
faults.
Monday, September 12, 2016
SNMP Simulators: build vs. buy
Faced with the prospect of simulating large network management
environments, the typical build vs. buy dilemma emerges: should you pay
for a commercial solution, or build one of your own?
There are several free open-source simulators available, promising to tilt
that equation in favor of "build": since a seemingly viable alternative is
already available, you'll just modify what's out there to suit your needs.
This will work out in only the fewest scenarios: the simplest small-scale
simulations. For most other uses, there are many pitfalls:
1. Meeting the requirements: You have to evaluate the best open-source
for your purposes, and you risk making a sub-optimal choice. You might
pick one, only to find out it does not handle your changing requirements;
2. Developer training: You have to train your developers on the chosen
solution(s), not only from a end-user perspective, but down to the nitty
gritty design, source code and build procedures. You are essentially
investing in something other than your core competency;
3. Quality: Open-source might be high-quality for commodity software
(Linux, OpenOffice), but in highly-specialized areas it usually has few
developers/maintainers, goes out of date, and results in lower-quality
software.
4. Scalability: Designs that work for a small number of simulated entities
usually will not for large numbers due to worse-than-linear behavior of
algorithms. This will usually result in unacceptable performance.
5. Beyond SNMP: Network management applications these days use more
than SNMP to access the managed entities. This requires an integrated
solution that simulates not only the SNMP interface, but also command-line
interfaces (Telnet, SSH), flow-based protocols (NetFlow, sFlow), Web services
(XML, SOAP, REST, etc).
6. Budget for software maintenance: The initial development task is
usually a small part of the total effort. At least one developer has to
continuously maintain and upgrade the software, post messages on some
user groups for getting it built and deployed but also try to get timely
answers for resolving bugs.
The end result is usually that you'll spend way more effort on the
"build" decision than the cost of the commercial solution would have
been to start with, impacting time-to-market, quality, support, etc.
Many large companies have already chosen to buy instead of spending
effort re-inventing the wheel. Their thinking is that it is better
to spend time and energy behind the companies' core product and services.
Do they know something you don't?
MIMIC SNMP Simulator has been on the market for 20 years. Simulators is all
that Gambit does and has hundreds of man years invested in. The end result
is a mature, high-quality, high-performance simulator that runs at most of
the large networking vendors world-wide. For example, reference customers
are vendors such as Lancope and Xirrus, and end-users such as Pepco and
SITA.
Combined with the other simulators in the MIMIC Simulator Suite you can
have a large realistic environment for development, testing, demo and
training of your network management application.
MIMIC runs on physical servers or the cloud and has been adapted to many
unforeseen uses. For example, Cisco runs MIMIC in combination with Prime
Infrastructure in their on-demand cloud platform dCloud.
environments, the typical build vs. buy dilemma emerges: should you pay
for a commercial solution, or build one of your own?
There are several free open-source simulators available, promising to tilt
that equation in favor of "build": since a seemingly viable alternative is
already available, you'll just modify what's out there to suit your needs.
This will work out in only the fewest scenarios: the simplest small-scale
simulations. For most other uses, there are many pitfalls:
1. Meeting the requirements: You have to evaluate the best open-source
for your purposes, and you risk making a sub-optimal choice. You might
pick one, only to find out it does not handle your changing requirements;
2. Developer training: You have to train your developers on the chosen
solution(s), not only from a end-user perspective, but down to the nitty
gritty design, source code and build procedures. You are essentially
investing in something other than your core competency;
3. Quality: Open-source might be high-quality for commodity software
(Linux, OpenOffice), but in highly-specialized areas it usually has few
developers/maintainers, goes out of date, and results in lower-quality
software.
4. Scalability: Designs that work for a small number of simulated entities
usually will not for large numbers due to worse-than-linear behavior of
algorithms. This will usually result in unacceptable performance.
5. Beyond SNMP: Network management applications these days use more
than SNMP to access the managed entities. This requires an integrated
solution that simulates not only the SNMP interface, but also command-line
interfaces (Telnet, SSH), flow-based protocols (NetFlow, sFlow), Web services
(XML, SOAP, REST, etc).
6. Budget for software maintenance: The initial development task is
usually a small part of the total effort. At least one developer has to
continuously maintain and upgrade the software, post messages on some
user groups for getting it built and deployed but also try to get timely
answers for resolving bugs.
The end result is usually that you'll spend way more effort on the
"build" decision than the cost of the commercial solution would have
been to start with, impacting time-to-market, quality, support, etc.
Many large companies have already chosen to buy instead of spending
effort re-inventing the wheel. Their thinking is that it is better
to spend time and energy behind the companies' core product and services.
Do they know something you don't?
MIMIC SNMP Simulator has been on the market for 20 years. Simulators is all
that Gambit does and has hundreds of man years invested in. The end result
is a mature, high-quality, high-performance simulator that runs at most of
the large networking vendors world-wide. For example, reference customers
are vendors such as Lancope and Xirrus, and end-users such as Pepco and
SITA.
Combined with the other simulators in the MIMIC Simulator Suite you can
have a large realistic environment for development, testing, demo and
training of your network management application.
MIMIC runs on physical servers or the cloud and has been adapted to many
unforeseen uses. For example, Cisco runs MIMIC in combination with Prime
Infrastructure in their on-demand cloud platform dCloud.
Subscribe to:
Posts (Atom)